Can we trust the Zero Trust strategy?
The concept of zero trust has been here for a long time. Is it possible to trust it? When, according to it, nothing can be trusted? Yes. Because we can verify it with practice.
Imagine a situation. All users, applications, end devices, and data are somewhere on the Internet. Users do not sit at the terminal keyboards and monitors in your office building, needing to be identified with an identity card upon entry. The only means of exchanging data with another organization is not just a heavily guarded dot matrix printer on the floor.
Is that your daily reality? At such a moment, we move from a state where we use explicit authentication instead of implicit trust.
If a user accesses from outside the network, we always verify that they have carried out second factor authentication (MFA). When an end device accesses corporate resources, we verify that it is indeed what it claims to be (MDM). When the device user accesses sensitive documents in the application, we verify that the data are protected by encryption and classification (MIP) and that it is a managed application (MAM).
At all times, we raise the level of our confidence that a given approach and activity can be trusted.
- Strengthen the trust in the user. Eliminate weak passwords. Implement MFA authentication. Monitor login activities. Eliminate passwords completely with Windows Hello.
- Ensure the trust in the device. Register the device to the MDM. Verify its health. Reduce the risk with a suitable configuration. Eliminate vulnerabilities with MDATP.
- Extend the trust in the applications. Connect the applications with MCAS. Block the access to unauthorized applications. Monitor their activities. Prevent unauthorized access with MAM.
- Do not lose trust in the data. Implement classifications with MIP. Protect the content with encryption. Do not allow unauthorized sharing outside the organization.
Do not trust anything. Always verify everything.
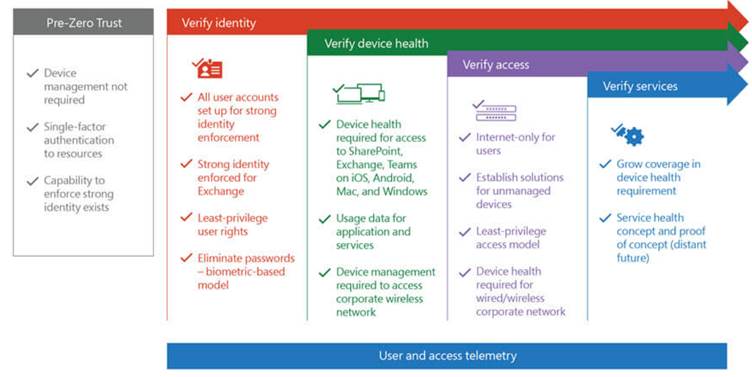
Figure 1: Concept of Zero Trust approach (resource: Microsoft)
Share on social media